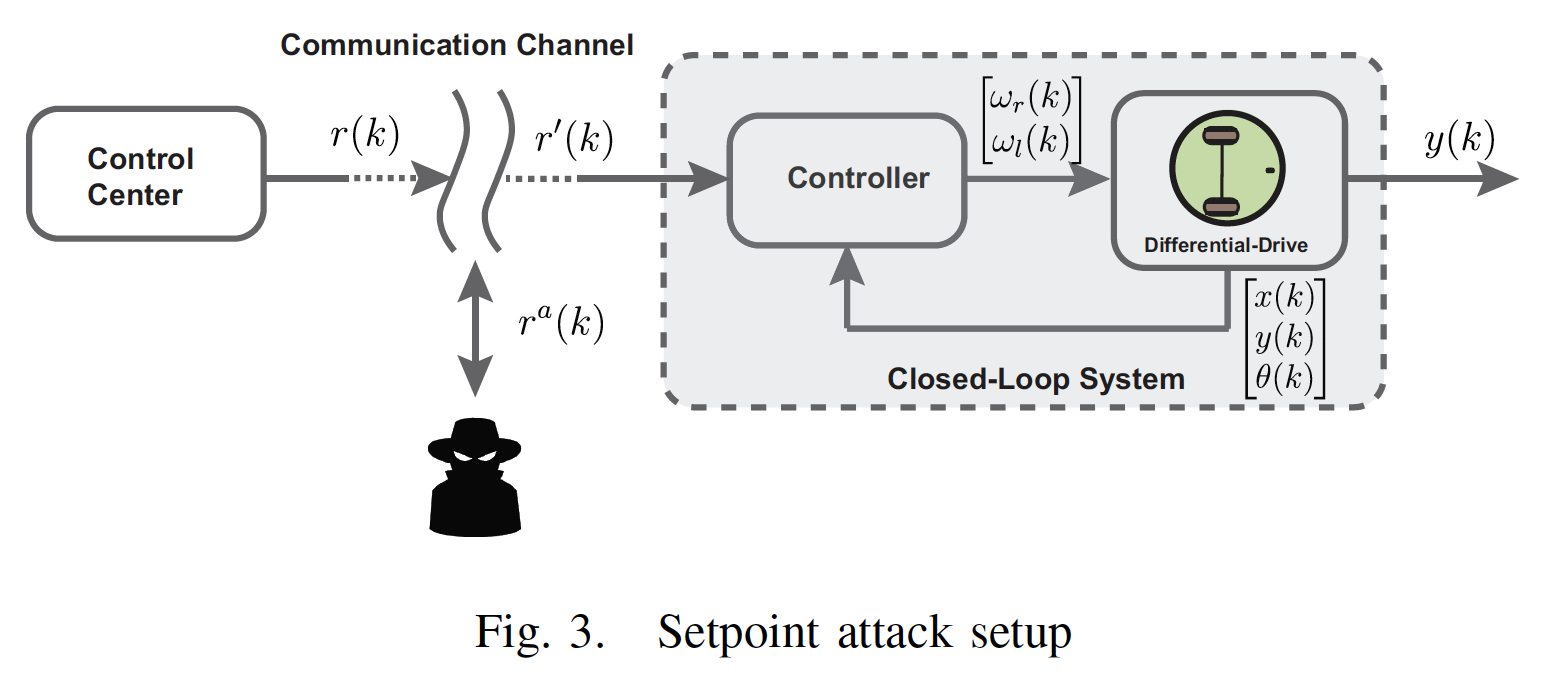
In this paper, we consider input-constrained differential-drive robots whose setpoint (reference) signals are sent by a remote control station via a wireless, and possibly insecure, communication channel. The objective is to develop an anomaly detector capable of revealing the presence of false data injections on the setpoint signal. Here, this is achieved by exploiting Command Governor (CG) supervisor module arguments and a detection unit. Specifically, two CG units, installed at the two ends of the communication channel, use a feedback linearized model of the vehicle dynamics to filter the reference signal according to the setpoints complying with the vehicle’s constraints. The detection unit, directly placed on the vehicle, takes advantage of the CGs actions to detect anomalies in the received reference signal. Moreover, a setpoint randomization procedure is proposed in order to avoid the existence of stealthy attacks. Simulation results involving a differential-drive robot are presented to show the effectiveness of the proposed solution.
M. Cersullo, C. Tiriolo, G. Franze', and W. Lucia. A detection strategy for setpoint attacks against di erential-drive robots. IEEE International Conference on Automation Science and Engineering (CASE), 2022