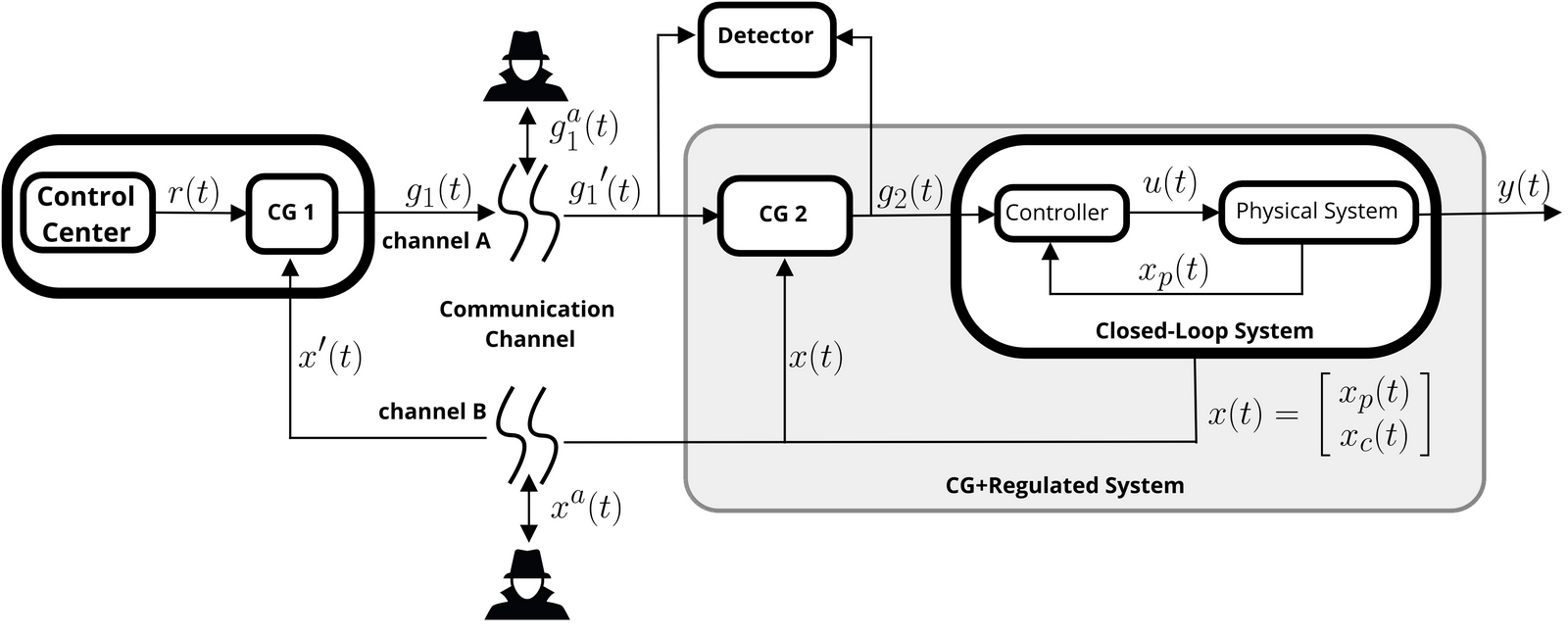
In this article, we face the problem of detecting setpoint attacks in networked control systems. We consider a setup where the reference signal (also known as setpoint) is generated by a control center remotely located with respect to a standard feedback controller. In this scenario, an attacker with sufficient resources can exploit the communication channel to alter the setpoint signal and ultimately affect the tracking performance of the control system. With respect to this problem, we propose a novel distributed control architecture that, taking advantage of peculiar capabilities of the command governor control paradigm, enables the detection of reference attacks. We formally prove that for constrained linear systems such detector exists. Moreover, by limiting the attacker's disclosure resources with superimposed cryptographically secure pseudorandom signals, we show that the absence of advanced stealthy attacks is also ensured. Finally, a solid numerical simulation investigating setpoint attacks on the flight control system of a single-engine fighter is presented to provide tangible evidence of the features of the presented methodology
W. Lucia, K. Gheitasi; M. Ghaderi, IEEE Transactions on Automatic Control ( Volume: 66, Issue: 5, May 2021)